Overview/Abstract:
There has been renewed interest in cybersecurity on the part of U.S. insurers. Accordingly, Gain Compliance has received numerous inquiries around its policies, procedures, and practices with regard to safeguarding confidential data.
This White Paper provides an overview of industry trends around third-party/vendor data security risks as well as a primer on Gain’s history and approach.
Background:
The recent focus on data security can be traced back to three trends:
- Regulatory activity: increasingly, state DOI’s are placing additional responsibility on insurers to safeguard information.
- High-Profile Incidents: data security breaches – such as one that exposed the personal information of over 200,000 U.S. policyholders to the dark web or another which led to the recent State Farm lawsuit – have forced a reevaluation of not only internal systems, but also the vetting processes for vendors.
- Industry Information Sharing: related to the above, this has become a perennial topic at IASA conferences and in other forums.
History:
As evidenced by tracking regulatory initiatives, industry focus on data security has waxed and waned over the past decade.
In recent history, two years of effort by the NAIC to craft and refine a best-practices approach for regulators culminated in 2017’s Insurance Data Security Model Law and the accompanying goal of its universal adoption within five years. This initiative was revisited by the NAIC in January, 2024 with a report of solid, but still incomplete, progress towards this objective:
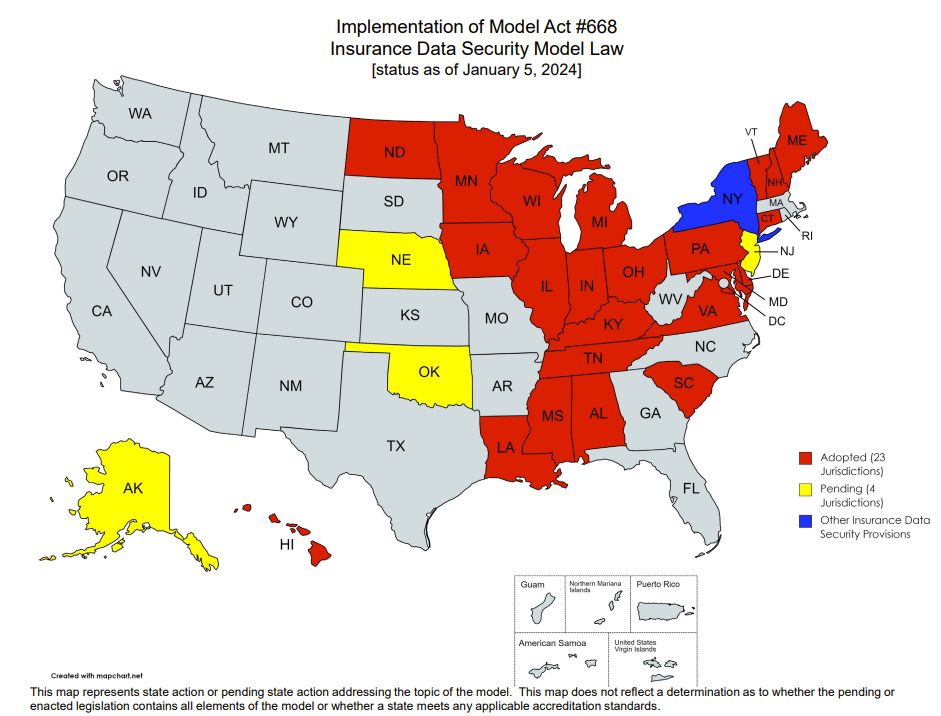
Notable on the chart above: as invariably occurs, there is state-based variation from the model law. In this case, New York introduced its own requirements in 2017 which were subsequently revised – first (very modestly) in 2020 and then (more extensively) in November, 2023.
Accordingly, each carrier operating in New York is required to attest annually that its Cybersecurity Program complies with 23 NYCRR Part 500:

Industry sentiment has cycled to renewed scrutiny on data security practices. Both broader adoption of NAIC’s model cybersecurity law as well as additional state-based variation appear inevitable.
Defining Vendor Risk
The risks of non-compliance with data security best practices and regulations are significant. Notably: these risks extend past a carrier’s internal practices and to those of all vendors used by the carrier.
The consequences of a data-security breach caused by a vendor are no less severe, expensive, or embarrassing than an internal breach. In fact, the two are indistinguishable: a policy holder whose personal data ends up on the dark web is wholly interested in the root cause of the issue and, quite rightly, will place blame on the carrier. So too will the plaintiffs’ attorneys.
An insurer’s nightmare scenario is to suffer not only the reputational and regulatory effects of a vendor data breach, but also the resulting legal actions. Such incidents are not uncommon, such as the repercussions of compromised data from a law firm in California, the class action against Progressive stemming from a third-party lapse, or the myriad lawsuits resulting from the SOVOS security breach.
Marrying the two topics together – the responsibilities of carriers around data security and third-party risks – begs the question of how to best screen vendors on their data security practices.
Best Practices for Assessing Vendor Risk:
Carrier Responsibilities:
The NAIC model law text, New York’s state-specific requirements, the numerous examples of high-stakes lawsuits, the persistent conversations at industry conferences on the topic – all drive home a clear message:
Carriers ultimately bear responsibility for any data security breach, regardless of whether the compromise was internal or caused by a contracted vendor.
How to best safeguard against this particular flavor or data security risk, then?
Interestingly, the answer differs from the most common approach used today.
Current Approach:
The industry standard process for third-party data security review is comprised almost exclusively of the collection of documentation.
The process typically starts with a vendor questionnaire. This is sometimes followed by a second round of data gathering in the form of interviews or additional information requests. The end result is that the carrier obtains a broad, albeit superficial and largely self-reported, concept of the vendor’s control environment.
Absent from this process is meaningful analysis of the information. Vendor risk review is often treated as a “check-the-box” activity. The goal, quite frankly, is to complete the procurement process expediently rather than to gain insight.
By way of an example of a limitation of this approach: a conventional data security questionnaire requires only basic attestation that there are policies in place around access to confidential data. Typically, the inquiry ends there. No follow-on analysis is performed to understand the actual effectiveness of the vendor’s written policies, or even the true extent to which the vendor conforms with these policies in practice.
A Spiderweb of Risk for Carriers:
When engaging with vendors, there is a cascading set of risks: the carrier is not only inheriting the risk of the contracted vendor itself, but all third parties connected to the vendor as well. Invariably, all software companies contract with their own sets of vendors; any downstream vendor which has access to the carrier’s confidential data is often classified as “in-scope.”
As seen with the SOVOS and Progressive data breaches, relying solely on the simple existence of policies regarding vetting and managing in-scope third parties was misguided, and the repercussions were expensive.
The better course of action on this single dimension of risk is a deeper dive to assess:
- The number and identities of any in-scope third party service provider;
- Proof of enforcing compliance with policies and procedures around managing in-scope third parties such as through testing and audits; and
- The vendor’s history of data breaches, including failures caused by its in-scope vendors.
On the last point: many carriers rightfully employ a one-strike policy with regards to data breaches: ANY incident is simply disqualifying. After all, how can a vendor’s practices be trusted to safeguard data in the future when their controls have been demonstrably ineffective in the past?
Further, the litigation and loss risk is simply too great. The decision to engage with a vendor which has a history of data breaches would be indefensible were a future data security breach to occur. The message that is communicated when engaging with a vendor with a history of data breaches is that the carrier simply does not take information security seriously.
Gain’s Approach:
In addition to the conventional certification (SOC2 Type II), routine activities (third-party penetration testing, regular security scans, in-scope vendor management), and best practices (policies and activities), Gain benefits from several additional factors:
- Modern Software: In the Statutory Financial Reporting market, Gain is, by far, the youngest solution provider. Founded in 2016, Gain has built a from-scratch, cloud-native software platform. While competitors’ products are based on legacy software code which is often ill-suited to current security challenges, Gain employed a modern approach in which today’s best practices are embedded in the software architecture.
- Focus: Gain’s single-product approach allows the company to channel all of its efforts to building and maintaining the best, and most secure, platform for Statutory Financial Reporting. This stands in contrast to Gain’s largest competitors which support myriad products across multiple markets.
- Development environment: Gain has deliberately architected and designed a standalone platform which, in sharp contrast to the competitors, is predicated on proprietary code written and maintained internally. Accordingly, and indicative of its commitment to data security, Gain contracts with a very limited number of in-scope vendors who, in turn, are subjected to a substantive vetting and management process.
- Reputation: Gain has earned a pristine reputation with regards to data security. The company takes its professional responsibility for customer data very seriously, including the ongoing investment required by a dynamic security environment.
Conclusion:
Data security breaches represent a violation of the trust by carriers to safeguard their policyholders’ information.
The stakes – in both reputational and financial terms – are high.
By no means is this an abstract risk for insurers; cautionary tales of data breaches abound. Yet, carriers continue to insufficiently address a key source of data security risk – vendors.
Vendor risk assessments must transition from a “check-the-box” process to meaningful analysis of vendor practices. This should include not just a collection of a vendor’s self-reported data of the control environment, but a critical assessment of the vendor’s effectiveness in implementing these controls.
